This is a guide on how Qloaked can help companies set up fully-secured vanity URLs for SaaS or ecommerce customers, without handling certificates or requiring any integration with external APIs.
The Vanity URL Problem in SaaS and Ecommerce
A common problem for SaaS companies who provide B2B services is offering white-labelling with custom vanity URLs for their customers. This may also affect ecommerce companies, particularly those who rely on whitelabelled affiliates to sell their products through branded websites which they don’t control.
In practice, this often looks like this:
- AcmeApp is a SaaS company providing helpdesk software to help companies support their customers
- Bluth Company is a client of AcmeApp
- Bluth Company wants to offer AcmeApp’s helpdesk to its customers via a custom domain at helpdesk.bluth.com
Until fairly recently, this was a simple thing to do – Bluth Company could just point a CNAME record for ‘helpdesk’ at AcmeApp’s servers.
However, the widespread requirement for secured, encrypted (via SSL/TLS) HTTPS connections means that simply pointing a CNAME is not enough – a certificate needs to be issued to protect the traffic running through to AcmeApp’s server.
For AcmeApp, this is a problem – there could be thousands of customers like Bluth Company, and provisioning and handling so many SSL certificates presents technical, customer support and legal challenges. Vanity URLs for SaaS or ecommerce are no longer a simple matter!
After facing the issue ourselves in several businesses, we decided a better solution could be offered – in this post, we’ll be running over exactly how SaaS companies can get started provisioning vanity URLs through Qloaked.
How It Works (Briefly)
Qloaked is a globally-distributed reverse proxy – essentially a ‘tunnel’ through which data to and from a website passes between the server and the customer’s computer.
A typical request to a website will pass through several ‘tunnels’ of this type, but Qloaked is special because it’s equipped with detection for insecure traffic, and scripts which run to secure the traffic if it’s detected. This functionality (technically known as ‘certificate provision’) happens in conjunction with Let’s Encrypt, the world’s leading solution for SSL certificate issuance.
Essentially, Qloaked acts both as a monitor for insecure traffic and, once the traffic is secured, the tunnel through which it flows.
If you’re keen to learn more about what’s under the hood at Qloaked, check out our How It Works page for further information.
Setting Up Qloaked for SaaS
To begin using Qloaked, you’ll need to sign up via signup page at https://app.qloaked.com/signup:
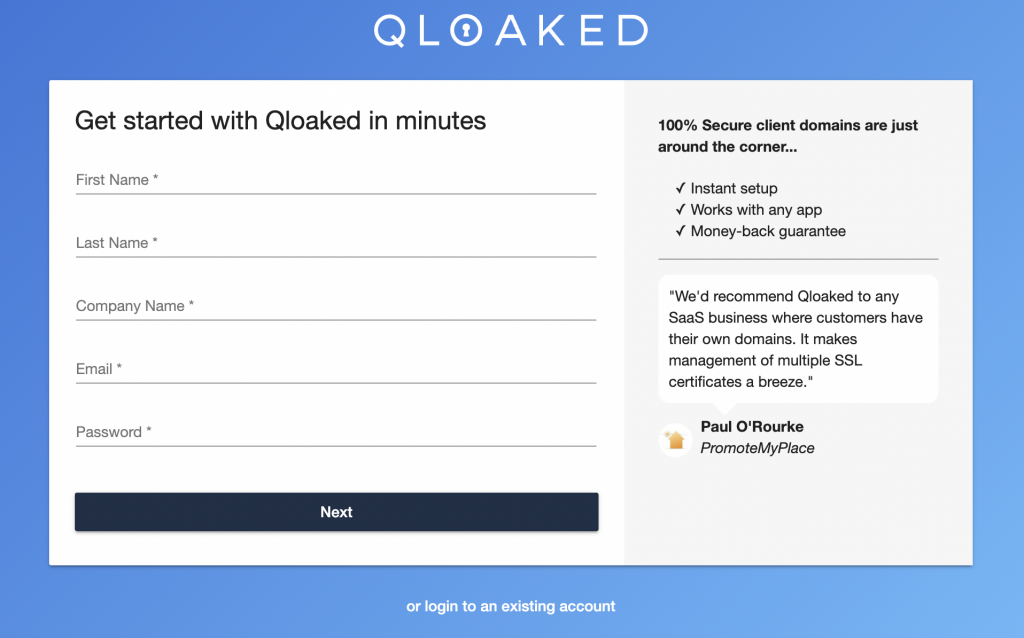
You’ll be asked for a credit card as part of this process, but we’ll only charge you after your 7 day free trial is completed. Find out more about how this works on our Pricing page.
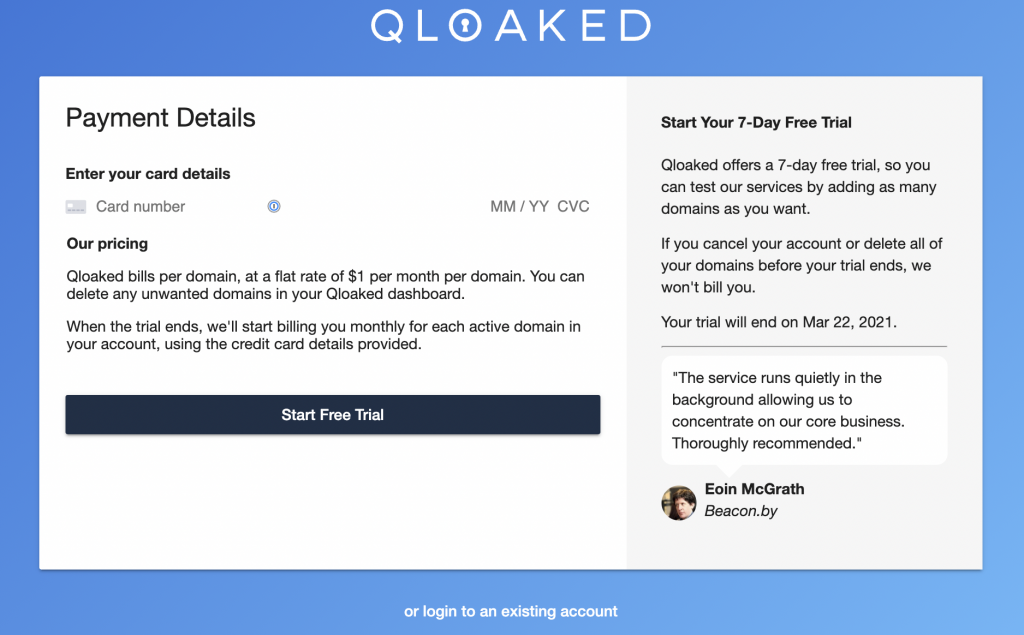
Note: If you *really* don’t want to add a credit card to see how Qloaked works, you can test the system by pointing a CNAME record of any domain (yep, any domain!) at magic.qloaked.com. You’ll be able to see how Qloaked provisions a certificate automatically, which will hopefully give you enough confidence to give the app a shot!
After signing up, you’ll need to enter some basic information about your app.
First up, enter a name for your application (e.g. “My App Production” or “My App Staging”).
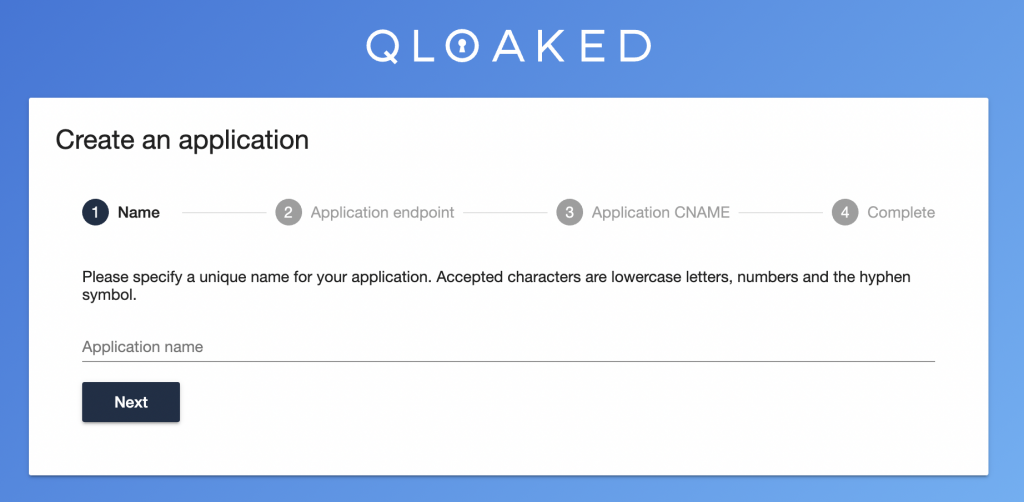
Then you’ll be asked for the Application endpoint – the address of your app server. This is the end of the Qloaked tunnel – the address to where traffic needs to be proxied. Note that you shouldn’t enter http or https on this address.
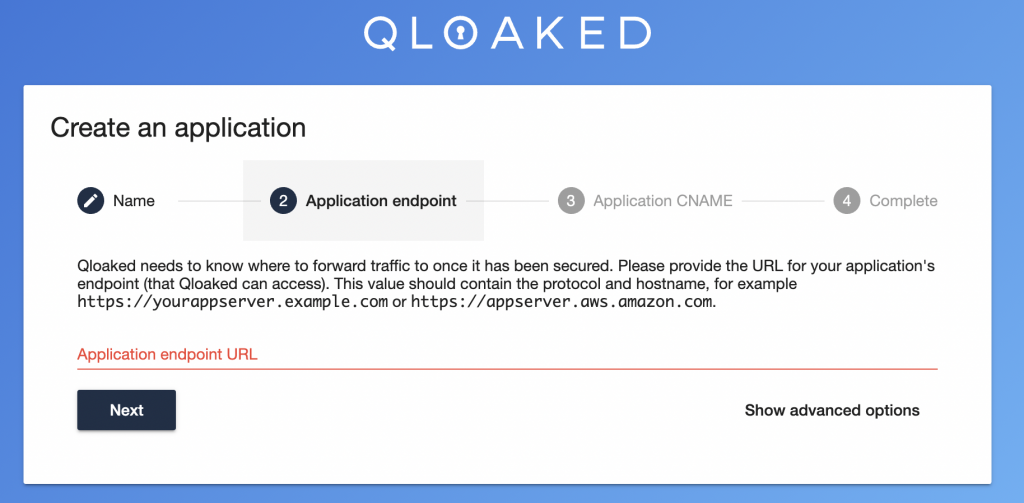
Finally you’ll need to enter the host which you’ll be using to point TO the Qloaked server. In our example above, this would be the address that AcmeApp would provide to Bluth Company to point Bluth Company’s custom domain at. Think of it as the entrance to the Qloaked tunnel.
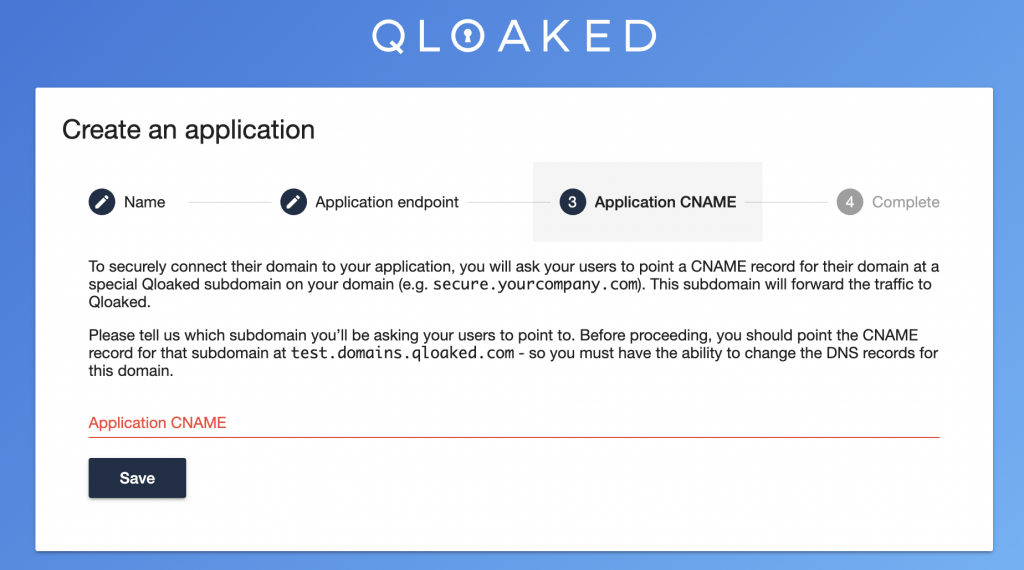
Click ‘Save’ and Qloaked will validate and complete your setup.
You’re done! You can now have clients point their vanity URLs (e.g. helpdesk.bluthcompany.com) at your secure endpoint (secure.acmeapp.com) and Qloaked will secure the connection automatically, proxying traffic onto your app’s endpoint (app-server.acmeapp.com).
Managing Vanity URLs with Qloaked
Once you’re inside, you’ll see that the admin interface offers a list of all of the secured domains attached to your account (screenshot deliberately blurred):
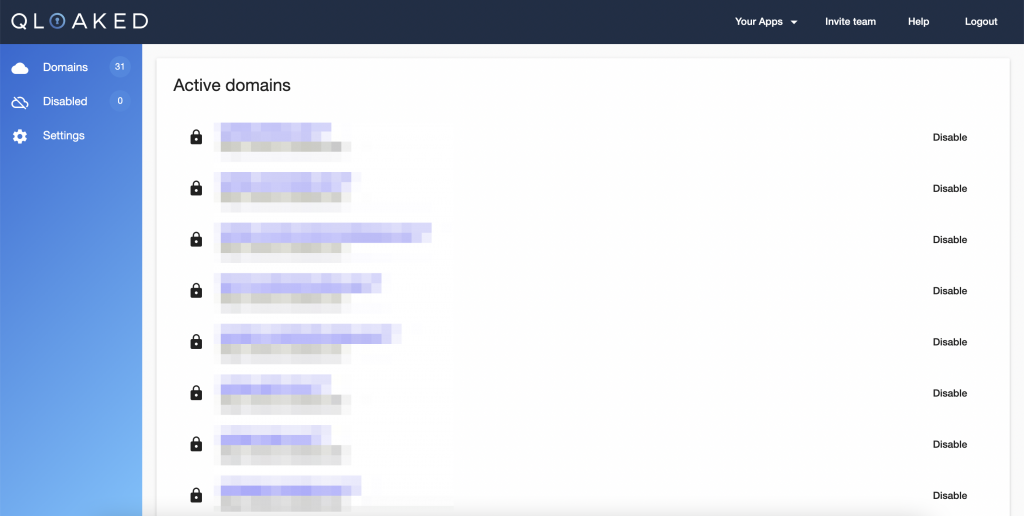
From the management screens, you can easily see whether a domain is secured or not (identified with the padlock) and when the SSL certificate is due to renew (mouse over the padlock to see this).
You can also delete any custom domains that you no longer wish to secure, by clicking the delete button.
By clicking on Settings, you can also invite team members to manage your domains.